The change from fixed size 0xF0 to sizeof(PS_SYSTEM_DLL_INIT_BLOCK) (which is 0x128 for V3 struct) causes memory corruption when using Windows 10 system files. **Before (working):** ``` constexpr uint64_t symtem_dll_init_block_fix_size = 0xF0; // Wine or WIN10 init_block.Size = symtem_dll_init_block_fix_size; // ... this->memory_->write_memory(ldr_init_block_addr, &init_block, symtem_dll_init_block_fix_size); ``` **After (broken):** ``` constexpr uint64_t system_dll_init_block_size = sizeof(PS_SYSTEM_DLL_INIT_BLOCK); // = 0x128 init_block.Size = system_dll_init_block_size; // ... this->memory_->write_memory(ldr_init_block_addr, &init_block, write_size); ``` **Symptom:** ``` Executing syscall: NtQueryVirtualMemory (0x23) at 0x18009d442 via 0x1800d4920 (ntdll.dll) Interrupt 41 Suspicious: Breakpoint at 0x1800ac7d8 (via 0x1800ac7d5) Executing syscall: NtQueryVirtualMemory (0x23) at 0x18009d442 via 0x180033579 (ntdll.dll) Executing syscall: NtQueryVirtualMemory (0x23) at 0x18009d442 via 0x180033579 (ntdll.dll) Executing syscall: NtQueryVirtualMemory (0x23) at 0x18009d442 via 0x180033579 (ntdll.dll) Executing syscall: NtQueryVirtualMemory (0x23) at 0x18009d442 via 0x180033579 (ntdll.dll) Bad address for memory image request: 0x5f0000 Executing syscall: NtRaiseException (0x168) at 0x18009fcd2 via 0x1800a0ee3 (ntdll.dll) !!! NtRaiseException: Code=0x80000003, Flags=0x0, Address=0x1800ac7d7, NumParams=0, HandleException=0 Emulation terminated without status! ``` **Root cause:** PS_SYSTEM_DLL_INIT_BLOCK has different sizes across Windows versions. It needs to detect the Windows version from ntdll and use the appropriate size. I will submit a PR to fix this issue soon.
Sogen is a high-performance Windows user space emulator that operates at syscall level, providing full control over process execution through comprehensive hooking capabilities.
Perfect for security research, malware analysis, and DRM research where fine-grained control over process execution is required.
Built in C++ and powered by the Unicorn Engine or the icicle-emu.
Try it out: sogen.dev
Warning
Caution is advised when analyzing malware in Sogen, as host isolation might not be perfect.
To mitigate potential risk, use the web version to benefit from the additional safety provided by your browser's sandbox.
Key Features
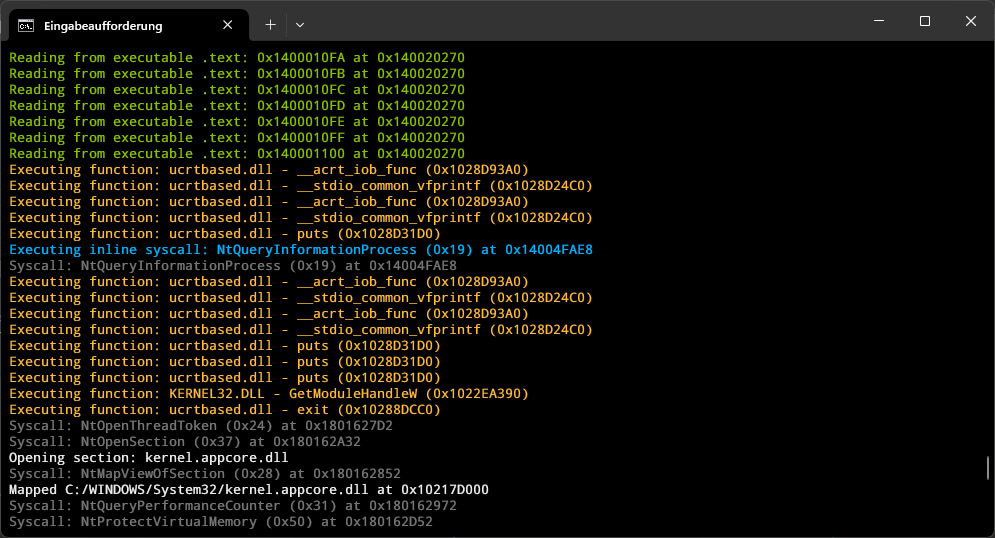
- 🔄 Syscall-Level Emulation
- Instead of reimplementing Windows APIs, the emulator operates at the syscall level, allowing it to leverage existing system DLLs
- 📝 Advanced Memory Management
- Supports Windows-specific memory types including reserved, committed, built on top of Unicorn's memory management
- 📦 Complete PE Loading
- Handles executable and DLL loading with proper memory mapping, relocations, and TLS
- ⚡ Exception Handling
- Implements Windows structured exception handling (SEH) with proper exception dispatcher and unwinding support
- 🧵 Threading Support
- Provides a scheduled (round-robin) threading model
- 💾 State Management
- Supports both full state serialization and
fast in-memory snapshots(currently broken 😕)
- Supports both full state serialization and
- 💻 Debugging Interface
- Implements GDB serial protocol for integration with common debugging tools (IDA Pro, GDB, LLDB, VS Code, ...)
Preview
YouTube Overview
Click here for the slides.
Quick Start (Windows + Visual Studio)
Tip
Checkout the Wiki for more details on how to build & run the emulator on Windows, Linux, macOS, ...
1. Checkout the code:
git clone --recurse-submodules https://github.com/momo5502/sogen.git
2. Run the following command in an x64 Development Command Prompt in the cloned directory:
cmake --preset=vs2022
3. Build the solution that was generated at build/vs2022/emulator.sln
4. Create a registry dump by running the grab-registry.bat as administrator and place it in the artifacts folder next to the analyzer.exe
5. Run the program of your choice:
analyzer.exe C:\example.exe